Vulnerability Assessment
Eliminating Known Weak Points Across Your Digital Landscape
Unveiling Known Cyber Risk Exposures
Whether comprehensively scanning for insecure system misconfigurations, detecting application vulnerabilities, or pinpointing authentication weaknesses, Redstone's automated scanning solutions leave no stone unturned. Our powerful scanning engine leverages the latest vulnerability intelligence to identify exposures with razor-sharp precision. Providing invaluable insights that only come from a scanning platform fortified by decades of cybersecurity experience. Rely on our proven scanning capabilities to illuminate your cyber risk blind spots and harden your attack surface against emerging threats.
Visibility
Gain full visibility into your cyber risk exposure across systems, networks and applications.
Efficiency
Cost-effectively identify exploitable vulnerabilities without the overhead of manual testing.
Prioritization
Prioritize remediation efforts with actionable insights from comprehensive scan results.
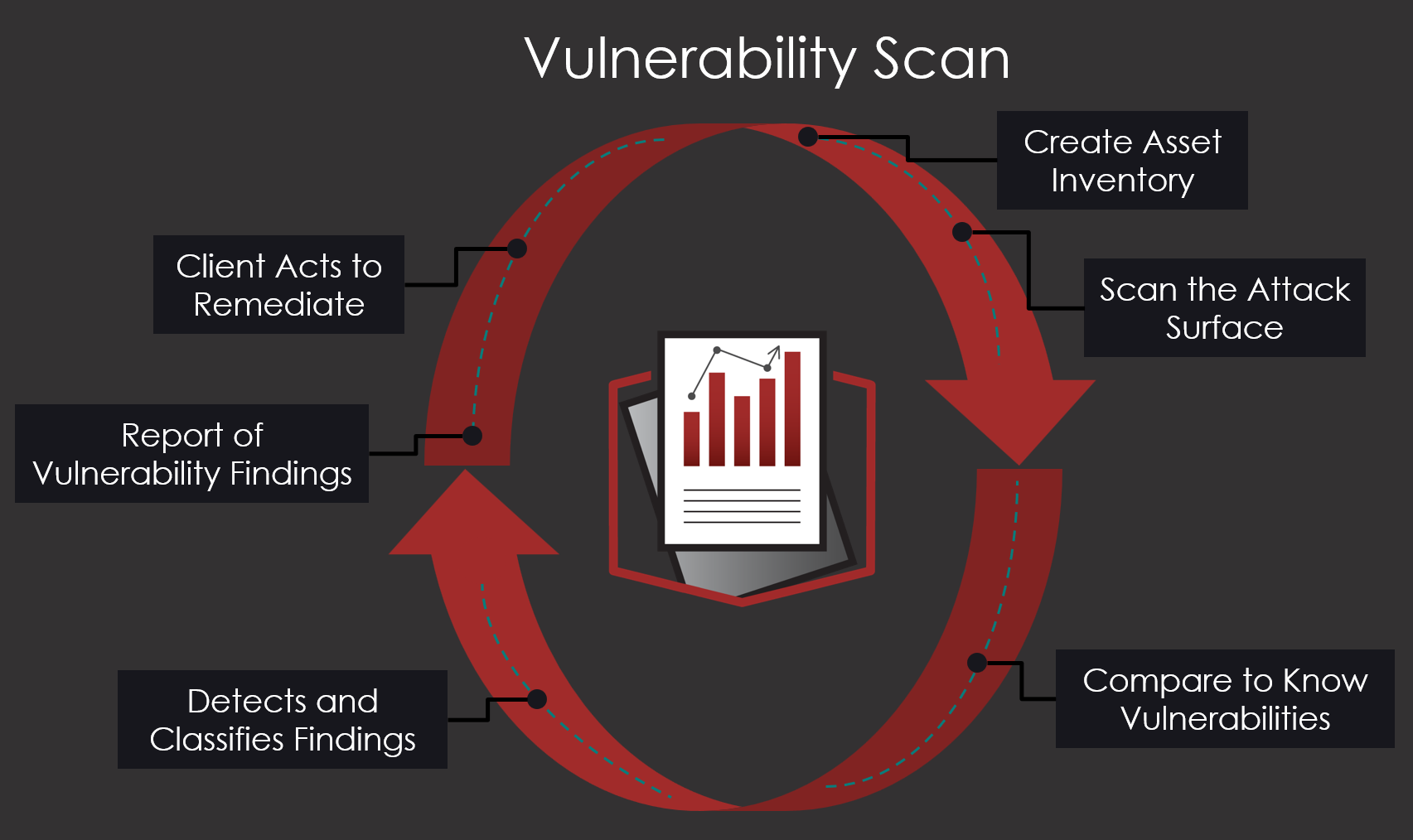
Preemptive Vulnerability Detection
Pinpoint outdated software, misconfigurations and other exploitable weaknesses before attackers can take advantage. Our vulnerability scans proactively illuminate potential entry points, giving you a head start on remediation. Stay one step ahead of cyber threats by identifying and addressing vulnerabilities through our comprehensive, automated scanning process - securing your digital assets before they are compromised.
Established Frameworks and Compliance: What do you fall under?
For organizations bound by stringent cybersecurity standards like NIST 800-171, PCI-DSS, SOC 2, and HIPAA, Redstone's vulnerability scanning solutions deliver comprehensive visibility into compliance gaps. Our automated scans rigorously assess your systems against up-to-date vulnerability intelligence, enabling you to identify and remediate weaknesses that could violate regulatory requirements.
Gain evidence-based assurance in safeguarding sensitive data and maintaining conformity through our in-depth vulnerability detection capabilities.
